September 28, 2004
La Ronde
(with apologies to Arthur Schnitzler)
Having swept aside my earlier prudery:
- My laptop is now paired with my bluetooth headset and my bluetooth phone.
- My bluetooth phone is paired with my laptop and my bluetooth headset.
- And the headset is paired with my laptop and my phone.
All very fin de siècle. But with all that pairing going on, there still seems to be a residuum of (serial) monogamy.
If I want to use the headset with my laptop, my phone must be either turned off or out of range. That’s not unreasonable; after all, I can’t expect the headset to function as an input/output device for both the laptop and the phone simultaneously.
But why is it that, if I want to sync the phone with the laptop, I need to turn off the headset first?
September 27, 2004
Collinear
A lot of people (myself included) got very excited by the fact that perturbative super Yang-Mills amplitudes seemed to take a very simple form when written in (super)-Twistor space and that, moreover, the tree-level amplitudes can be recovered very elegantly from a topological string theory with target space the aforementioned super-Twistor space. But my ardour cooled considerably when it became apparent that, when one went to the one-loop level in the Yang-Mills, the aforementioned topological string theory would produce not just super Yang-Mills, but super Yang-Mills coupled to conformal supergravity.
Moreover, it appeared that the known one-loop amplitudes were not easily interpretable in terms of a twistor string theory. One could easily identify contributions in which the external gluons are supported on
- a pair of lines in twistor space (connected by two twistor-space “propagators”)
- a degree-two genus-zero curve (with a single twistor-space “propagator”)
- of the gluons inserted as above, but with the gluon inserted somewhere in the same plane as the rest.
This last type of contribution is hard to reconcile with some sort of twistor string theory.
It now appears that this pessimistic conclusion was a bit too hasty. Cachazo Svrček and Witten have traced the problem in their earlier analysis to a sort of “holomorphic anomaly.” Their criterion for collinearity in twistor space was that the amplitude should obey a certain differential equation. However, the differential operator in question, rather than annihilating the amplitude, give a -function whenever the momentum on an internal line is parallel to one of the external gluon momenta. It’s just a glorified version of
The amplitude “really” receives contributions only of types (1) and (2). The apparent contributions of type (3) come from exceptional points in the integration over loop momenta, where an internal momentum is collinear with one of the external gluons.
I wish I’d thought of that…
September 26, 2004
And now B2
First there was an itex2MML plugin for MovableType. Then I ported it to WordPress. Now Scott Bruns has ported the plugin to B2evolution.
So, in at least three different blogging systems you can type $\int_{-\infty}^\infty e^{-x^2} = \sqrt{\pi}$ and have appear in its stead.
In Scott’s honour, I’ve released another minor revision (version 0.9) of the itex2MML executable, squashing a couple more bugs. The source and a MacOSX binary are available from the usual place.
September 19, 2004
Best. Spam. Ever.
I just received the following message in my inbox.
From: scdomains@yahoo.com Subject: How one can become a terrorist? Date: September 19, 2004 2:11:34 PM CDT To: distler@golem.ph.utexas.edu Received: from 211.243.217.138 ([211.243.217.138]) by golem.ph.utexas.edu (8.13.1/8.13.1) with SMTP id i8JJ7V8C019847 for <distler@golem.ph.utexas.edu>; Sun, 19 Sep 2004 14:07:33 -0500 (CDT) Message-Id: <2004099482.27828396@shadowcrew.com>Welcome to our web site www.shadowcrew.com/phpBB2/index.php
Please use http://63.240.81.5 in case of our domain outage.
You’re invited to shop for large selection of bombs and different kinds of rockets such as surface-to-air, surface-to-surface and weaponry available at reduced price. With the following types of rockets you will be able to commit terrorist attacks, destroy buildings, electric power stations, bridges, factories and anything else that comes your mind. Most items are in stock and available for next day freight delivery in the USA. Worldwide delivery is available at additional cost. Prices are negotiable.
Please feel free to inquire by ICQ # 176928755 or contacting us directly:
+1-305-592-2222
+1-919-319-8249
+1-314-770-3395Today special:
******* AIR BOMBS *******
OFAB-500U HE fragmentation air bomb
Fuel-air explosive air bombs -Not in stock
BETAB-500U concrete-piercing air bomb
ZB-500RT incendiary tank
500-KG SIZE RBK-500U unified cluster bomb
RBK-500U OAB-2.5PT loaded with fragmentation submunitions
RBK-500U BETAB-M loaded with concrete-piercing submunitions-Not in stock
RBK-500U OFAB-50UD loaded with HE fragmentation submunitions******* UNGUIDED AIRCRAFT ROCKETS *******
Main-purpose unguided aircraft rockets
S-8 unguided aircraft rockets
S-8KOM
S-8BM-Not in stock
S-13 unguided aircraft rockets
S-13, S-13T, S-13-OF, S-13D, S-13DF
S-25-0
S-25-OFM
S-24B -Not in stock
RS-82
RS-132-Not in stock******* ROCKET PODS *******
B-8M pod for S-8 rockets
B-8V20-A pod for S-8 rockets
B-13L pod for S-13 rocketsRecently received *NEW*
Hydra 70 2.75 inch Rockets
Air-Launched 2.75-Inch Rockets
FIM-92A Stinger Weapons System
Stinger 101: Anti-AirOur clients are well known Al-Qaida, Hizballah, Al-Jihad, HAMAS, Abu Sayyaf Group and many other terrorist groups. We are well known supplier in the market and looking forward to expand our clientage with assistance of Internet.
Do not hesitate to contact us via ICQ # 176928755
Impatiently awaiting for your orders, ShadowCrew
Evidently, this unsavoury site has been the subject of several joe-jobs in the past. In paranoid times like ours, one wonders how this one will go over…
September 17, 2004
Skype

… rhymes with hype. Yes, the bête noire of VoIP from the folks who unleashed KaZaA.
I downloaded the MacOSX client, and bought myself 10€ worth of SkypeOut credits. Calls to other skype users are free. Calls to POTS phones in North America, Western Europe, Australia and Chile are 0.017 €/min. Israel is 0.026 €/min and, should I ever feel the need to call (say) Angola, the price is a mere 0.142 €/minute.
My first act was to call my sister in California, whose reaction was that I sounded like I was talking over SpeakerPhone. Since I was using the built-in microphone in my laptop, that was an accurate assessment. Then I invested1 in a BlueTooth headset. The audio quality is fantastic, and I can use it from across the room.

“Free?” I hear you say. “How do they intend making money?” Indeed, the Skype Technologies business model seems a bit dodgy. Granted, the peer-to-peer nature of the skype network (a legacy of its P2P filesharing heritage) keeps their costs very low. They don’t need to maintain a server infrastructure that a centralized VoIP network would require. Still, their costs are nonzero and the only revenue stream I see is the 10 or 20 € that people shell out for SkypeOut credits. But surely these prices are pretty close the cost of peering with PSTN. Moreover, after you’ve called your friends in Australia a few times, they may get the idea and download skype too; thereafter, you talk for free. How does Skype Technologies intend to make money? Perhaps they’re relying on the slightly obscure provision that your remaining SkypeOut credits expire 180 days after your last credit purchase. If you want to maintain the ability to make SkypeOut calls, you need to shell out a minimum of 20 €/year, even if your actual usage is much less. And there’s talk of rolling out other “premium” services, like voice-mail, at additional cost. But, however you slice it, this is by far the cheapest deal on long-distance you can find anywhere. You have to marvel at their cost structure, if they can make a profit under these conditions.
Another thing I wondered about is the encryption. Skype-to-skype calls use 256-bit AES encryption. To exchange AES session keys, skype uses 1536 to 2048 bit RSA public key encryption. But how do the two skype clients verify each others’ public keys? The FAQ says, “User public keys are certified by the Skype server at login.” The skype client allows you to login as any skype user. Presumably that means that the RSA key-pair cannot be stored locally. Does that mean that the client generates a new key-pair each time you login? Does anyone know how it actually works? Such questions would be all laid to rest if, like any good encryption product, skype were open-source, but it ain’t…
One of the virtues of skype, inherited from KaZaA and its P2P brethren is that it “just works,” even from behind a NAT router or firewall. The way it does this is to cheat. Skype uses port 80 (http) and port 443 (https), which are almost never blocked by even the most assiduous of firewalls. Clients behind NAT routers typically can’t accept incoming connections. So skype relies on “supernodes,” clients on the open internet which can accept incoming connections, to relay traffic between those clients which cannot.
Usurping a well-known port for a totally-different protocol is not good sportsmanship. And it limits the usefulness of the program. Obviously, machines behind firewalls or NAT routers can’t become supernodes. Neither can the MacOSX or Linux clients; not being SUID-root, they can’t bind to a privileged port. Nor can a Windows machine running a web server. This artificially limits the pool of potential supernodes, making the skype network less robust than it could be.
Skype could have used a distinct high-numbered port2 (like any other new application). Most firewalls allow outbound connections to high-numbered ports. Only in a small fraction of cases – those with really draconian firewalls in place – would using a high-numbered port have prevented skype from working. And those are the cases where the IT managers probably have a good reason for firewalling those outbound connections. By masquerading as http(s), all you do is piss off your IT managers, who probably don’t want skype on their network and will take steps to ban it anyway.
Of course, some will ban skype just because of its connection with KaZaA. CERN bans it from their network and the stated reason seems a little shaky to me. Aside from the unsavoury nature of its cousins, the P2P filesharing programs, I don’t see why skype supernodes would pose an undue burden on the CERN network. It seems to be more of an “It’s the principle of the thing!” issue, than an actual concern about bandwidth or network performance.
Another complaint, voiced in some circles, is that skype doesn’t support the SIP Standard for internet telephony. Well, neither does iChat-AV3 (or AIM) and even the absence of an InstantMessaging Standard has not slowed their uptake. For me, skype-to-skype calls fill exactly the same niche as iChat-audio. Skype has slightly better sound quality; iChat also offers video capability. SIP uses centralized servers for presence and directory information. Skype’s P2P nature (even the user-directory is decentralized) obviates the need for centralized servers. SkypeOut, which presumably does require a server infrastructure (and which, for me, distinguishes skype from iChat and its brethren), doesn’t really need SIP either.
Standards are crucial for interoperability, but that only matters when you have someone you need to interoperate with. Skype has rocketed to the top of the VoIP heap because no one else had offered anything nearly as easy to set up, as high in audio-quality and as cheap to use.
Most of the other players in the VoIP game (both the Telcos and the “upstart” newcomers) seem dedicated to reproducing the “telephone experience” in all its details — from handsets to dialtones to the monthly bill — over the packet-switched internet instead of the circuit-switched PSTN. Skype has reconceived VoIP as a desktop PC application (though many PDAs and even some phones support skype). At the same time, they’ve reconceived what kind of network infrastructure is required to support VoIP.
When skype has some actual competition it needs to interoperate with, adding SIP support shouldn’t be that hard. Me, I’m not particularly worried. Right now, I have some phone calls to make…
1 If you don’t have bluetooth on the motherboard (a BTO option on some Mac models) you’ll need a bluetooth USB adapter. Don’t assume, just because an adapter is “Compatible with MacOSX 10.2 and later” and “Supports the Bluetooth Headset Profile” that it will support the Headset Profile under MacOSX. There’s only one which will, and even that one will only do so after flashing the firmware, thereby rendering the unit unusable on any non-Macintosh machine. So much for “It just works™!”
2 Actually, the MacOSX skype client does listen on port 54045 (both tcp and udp). This wasn’t mentioned anywhere in the documentation. In fact, it looks like skype may use ports 80/443 only when all else fails. Right now, I’m connected to a supernode on some more-or-less random high numbered port.
3 iChat does use SIP for transmitting session-initiation requests, but it doesn’t actually use SIP to initiate the VoIP sessions themselves. Still, nobody complains about the fact that iChat isn’t really SIP-compatible.
September 15, 2004
Spin Chains
Ever since I failed to mention it in my coverage of Strings 2004, I’ve been meaning to say something about spin chains and anomalous dimensions in gauge theory. It’s really pretty stuff and seemingly very deep.
The story starts with a paper by Minahan and Zarembo and a followup by Beisert, Kristjansen and Staudacher. We’ll work in the large- limit, and study an expansion in the 't Hooft parameter, . We are going to compute the anomalous dimensions of the spinless superconformal primary fields transforming as some representation of the R-symmetry.
In general, because of operator mixing, this is a messy business. But the observation of Minahan and Zarembo is that operators consisting of a trace of a product of scalars, which transforms in the representation of form a closed set under renormalization. If we write the six scalars in the multiplet as
then a trace of a product of ’s and ’s (in any order) transforms in representation and has engineering dimension and so cannot mix with any operators involving gauginos or field strengths or covariant derivatives. Moreover, each such operator
or
can be thought of as a state of an spin chain, where we identify and . Minahan and Zarembo noticed that matrix of one-loop anomalous dimensions,
is none other than the Hamiltonian for the Heisenberg spin chain. This Hamiltonian is integrable. Beisert et al showed that dilation operator up to 2 loops is, again, an integrable spin-chain Hamiltonian, and this structure seems to persist to higher loops as well.
The interpretation of the higher conserved charges (which can be constructed) remains mysterious, as does the origin of this integrable structure. There’s been a whole flurry of work on this subject. For a flavour of what’s been going on, you can check out the recent, somewhat telegraphic review by Beisert.
September 6, 2004
Billboard
Most of the billboards around the UT campus feature alcohol and/or scantily-clad women. But one austere black-on-white billboard on Guadelupe has intrigued me as I drive past it on my way home from work:
.com
If you find the aforementioned prime (I, personally, was surprised at how far out in the decimal expansion of one has to go to find it), and visit the corresponding website, you are greeted with a second puzzle
__________
and you’re told to visit a second website, using “Bobsyouruncle” as a Username and the value of as a password.
When you get there, you’re greeted with an offer to submit your resumé … to Google.
One thing we learned while building Google is that it’s easier to find what you’re looking for if it comes looking for you. What we’re looking for are the best engineers in the world. And here you are.
As you can imagine, we get many, many resumes every day, so we developed this little process to increase the signal to noise ratio. … You’ll find links to more information about our efforts below, but before you get immersed in machine learning and genetic algorithms, please send your resume to us at …
Now that’s a sexy advertising campaign.
Labour Day
This is, perhaps, the last Labour Day of the Bush presidency, so it behoves us to look, once again, at employment under his stewardship.
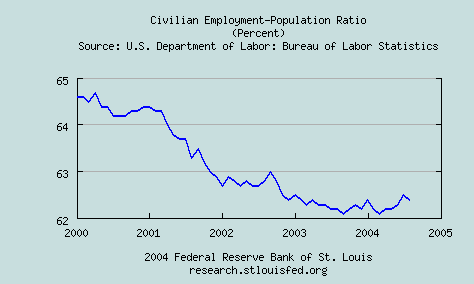
Employment, as a fraction of the working-age adult population slid from 64.4% when Bush took office, to 62.4%. (All employment statistics cited are monthly, seasonally-adjusted, figures from the Saint Louis Fed.)
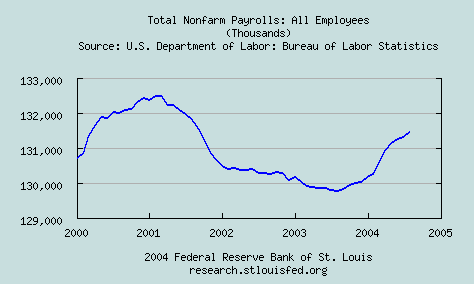
Total Non-Farm Payroll Employment slid from 132.4 million when Bush took office to a trough of 129.8 million a year ago, recovering somewhat to 131.5 million. He will leave office with the dubious distinction of being the first president since Herbert Hoover to preside over a net loss of jobs, not as a fraction of population, but in absolute terms.
Meanwhile, the Federal Budget has gone from an annual surplus of $236.4 billion in FY 2000 to an annual deficit of $444.7 billion for FY 2004, with red ink as far into the future as the eye can see.
Sobering thoughts for this Labour Day.
September 3, 2004
Topological Vertex
There’s a very interesting paper by Li, Liu, Liu & Zhou (my, how that rolls off the tongue!), which provides a mathematical formulation of the topological vertex by Aganagic, Klemm, Marino & Vafa. The claim of the latter is that one can construct the higher genus topological A-model invariants for a noncompact toric Calabi-Yau by summing trivalent Feynman graphs, whose vertex is the aforementioned “topological vertex.”
LLL&Z put this proposal on a firm mathematical footing using relative Gromov-Witten theory (which, if I understand correctly, has not previously found a role on the physics side).
Bogdan Florea pointed out to me that the LL&Z did not prove that their formula is equivalent to AKM&V’s formula for the topological vertex, though they have checked, in examples, that the two formulæ agree.
Building a Better Mousetrap
Anyone who’s followed this weblog, for any length of time, knows that a fair amount of energy went into ensuring that it produces valid XHTML+MathML. Starting with an off-the-shelf CMS like MovableType or WordPress, and “bullet-proofing” it, so that you can safely serve XHTML+MathML with the correct MIME-type is a tedious process.
I wrote a series of tedious posts (I,II,III,IV,V), recounting my own experience with MovableType.
So my ears definitely pricked up when Henri Sivonen, in the comments to one of Anne van Kesteren’s posts, argued that a truly XML-based CMS would make this task easier.
At their core, CMSs in general (or weblogging systems in particular) are very simple. They receive content (posts, comments, trackbacks, …), which they run through some templates to produce pages.
It’s these templates that Henri wants to improve. “Tag-soup” languages, like PHP, operate on strings to produce other strings (which might or might not turn out to be well-formed XML). Maybe your templates are correct, and will turn valid input into valid output (out of the box, both MovableType and WordPress mostly do so), or maybe you’ve attempted to customize them, and they now produce invalid poo.
Henri’s templating system acts on document trees. Well-formedness is built-in. Only at the very end, is the output run through an XML serializer to produce a web page. Naïvely, it sounds a little like XSLT, which allows you to specify rules for transforming one XML document into another.
Henri and his collaborators have a paper, describing the system, and Henri has just released some source code.
Personally, I don’t think that it’s the templating system that’s the real Achille’s heel of today’s CMSs. I, rather dismissively, summarized that part of the story with a
Before we plunge in, it would be wise to make sure your pages are valid XHTML 1.1.
in my writeup. The real problem is dealing with dodgy content. Much of it (comments, trackbacks, etc.) comes from sources who neither know, nor care about the exigencies of producing valid XHTML. Henri’s stance seems to be, “If it doesn’t parse to valid XML, reject it.” Which probably means you’re not going to have a whole lot of content on your Sivonen-powered weblog. Gently guiding users in producing valid content is the hard problem that no one has really addressed.
Still – aside from a few folks like yours-truly, who’ve cobbled something together – Henri’s system (which involves more than just the templating engine that he’s released), is the only one which validates the content on the way into the database. Two years after starting this weblog, I’m still waiting to see content-validation offered as even an optional feature on any mainstream CMS.
September 1, 2004
MT 3.1
As you may have noticed, we’re now running MT 3.1.
Most things work, but Search is somewhat screwed up at the moment. The Search CGI script in MT 3.1 does not clean up properly after itself. As a consequence, if you run a search, and then run another one, it thinks that your first search is still ongoing, and counsels you on the virtues of patience.
The best I can say, at the moment, is to wait 60 seconds before running a second search. Hopefully, a fix will be forthcoming. [Update: I have a temporary fix in place. It’s not ideal, but Search is working properly again.]

 Posts with this logo use
Posts with this logo use