March 30, 2003
A Different View
The reportage from the “embedded” reporters on the Iraq war is certainly compelling, if somewhat blinkered. There is — both metaphorically and physically — not much visibility from the inside of a Bradley APC.
For another perspective, check out the coverage from ArabNews.com, Saudi Arabia’s “first English Daily”. One of their reporters in particular, Essam Al-Ghalib has been in Basra and has a riveting series of dispatches from Southern Iraq: I, II, III.
March 29, 2003
Sendmail 8.12.9
Sigh. And I thought I would have a quiet weekend doing my taxes.
Michigan Residents: Use NAT, Go to Jail
Ed Felten points out that the State of Michigan has made it a felony to use IP Masquerading, Firewall, or VPN software.
The punishment for hooking a NAT router to your cable modem or using a VPN to connect to the LAN at work (“conceal the existence or place of origin or destination of any telecommunications service.”)? Up to 4 years in jail and a $2000 fine.
Manufacturers of DSL Routers and authors of software with these capabilities are subject to the same penalties.
Michigan residents: you have until Monday, March 31 to comply.
Other states (including my own) are considering equally mad legislation.
March 28, 2003
Pity the Freshmen
I’m teaching Freshman Mechanics this semester. Not exactly the most uplifting of subjects. Still, even here, one can find surprising tidbits of beauty.
Consider a pencil (a uniform rod) balanced on its tip. As the rod begins to fall, the tip is held in place by the force of static friction exerted by the table.
- No matter how large the coefficient of static friction, , the rod will reach a critical angle, , at which it will begin to slide.
- For small , the tip will slide the opposite direction from the direction of fall. For large , the tip will slide in the same direction as the direction of fall.
- For very large , the critical angle (measured from vertical) at which the tip begins to slide is °
- There’s a critical value of , at which the behaviour changes abruptly. Below , the tip begins to slide opposite the direction of fall at a critical angle which approaches ° as we approach from below. Above , the tip begins to slide in the same direction as the direction of fall at a critical angle which approaches ° as we approach from above.
While these results sound mysterious and complicated, there is nothing but really elementary Freshman Physics at work.
That’s beautiful.
March 25, 2003
Javascript Bug
Well, I faced an interesting choice.
My Comment Popup used to have a functioning “rememberMe” javascript. But it did not render MathML (since the Content-Type was set to “text/html”).
I changed this to “application/xhtml+xml” when served to Mozilla. Alarmingly, doing so somehow breaks the aforementioned javascript.
If any of the experts have a fix, I’d love to hear it. I suspect, though, that this may be a Mozilla bug.
Update: It’s not a “bug, it’s a “feature”. When served as a text/html, the document is governed by the DOM for HTMLDocument. Firing up Mozilla’s DOM Inspector, (I’ve never done that before!) we see that, indeed, HTMLDocument has a cookie attribute. And we can refer to document.cookie in a Javascript to get at it.
When served as a application/xhtml+xml, Mozilla says the document is governed by the DOM for XMLDocument. And, firing up the old DOM Inspector again, we discover that … whoops! … there is no cookie attribute for XMLDocument, and not a hint of how to access the document’s associated cookies.
This surely cannot be what the W3C had in mind when they said XHTML 1.1 documents should be served as application/xhtml+xml.
Does anyone understand this stuff? I don’t; I am only dimly mouthing words I found on the internet. But if the above description is correct, the situation is utterly, criminally brain-dead. Whadya mean one can’t have cookies in XHTML?
March 24, 2003
War Blogs
In case the incessantly repetitious coverage of CNN/FoxNews/… isn’t enough for you, check out the indefatigable Sean-Paul Kelley, who’s providing seemingly round-the-clock news aggregation about the war. Or, for a different perspective, try the enigmatic Raed.
It comes as no surprise, but things are getting ugly.
March 21, 2003
Strangelove
No, not the creepy National Security Adviser from Stanley Kubrick’s classic film, the free MacOSX utility from Pygmy Software.
I get a lot of Microsoft Word documents in email. I don’t have Word, or any other Microsoft software, except for a stray copy of Internet Explorer that I use to test web pages. So these Word documents are sent directly to the trash unopened.
I 'spose I must be missing the occasional piece of important information. But, if the senders can’t be bothered to send their message in a universally-readable non-proprietary format, I figure they must not have thought it very important either. Anyway, no one has ever complained …
Unfortunately, my excuse ( “Very_important.doc ? I don’t think I can read that document format.”) is crumbling, thanks to the aforementioned utility. Drag an MS Word document onto Strangelove,
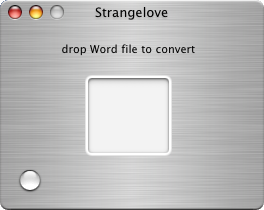
and it gets converted (using antiword and ghostscript) to PDF.
I guess I’ll have to find another excuse …
March 19, 2003
Let Slip the Dogs of War …
So it’s begun. Early Thursday morning (Iraqi time) the assault on Iraq began, with F117 stealth bombers, tomahawk cruise missiles, F18 strike fighters …
I pray that their victory will be swift, and that casualties (on both sides) will be light.
Meanwhile, the 82nd Airborne has launched a massive operation in southern Afghanistan. Apparently, they believe that Osama Bin Laden is to be found in the mountains near Kandahar.
May they, too, be successful in their objectives.
March 18, 2003
Fiber, Bandwidth, and Those Crooks at WorldCom
Brad DeLong’s blog has a great discussion going about WorldCom’s recent write-down of the value of their fiber network (now valued at 1/4 of what they paid for it).
He seems to be sympathetic to the idea that they were blindsided by the advent of Dense Wavelength Division Multiplexing (DWDM) in the mid 1990s. I don’t think that’s the explanation, but check out the discussion and judge for yourself.
March 16, 2003
Idle Hands
Well, I was wrong. The culprit in the massive UT identity theft case was, apparently, a junior CS major at UT with too much time on his hands.
Back when I was in school, the CS majors stumbled sleepily from one massive programming assignment to the next. Hard to imagine one of them having the time or energy to hack into the personnel database.
And this was not a small undertaking. Over the space of 5 days, his program made over 2.6 million database queries (that averages out to more than 22 thousand queries/hour, with peaks — according to the American Statesman article — of 72 thousand queries/hour).
What I don’t quite get is: why? I mean, after the first couple of hundred database queries, you’ve netted yourself a few SSN’s and surely intellectual curiosity has been satisfied. Your program works, the database is vulnerable, and a brute-force attack is clearly practical. If you stop now, probably no one will be the wiser.
If you decide to continue, why use your home computer and make no attempt to cover your tracks? Surely, after a couple of million database queries, it’s likely UT’s ITS folks will begin to notice that something’s afoot.
Maybe Mr. Phillips is hoping to parlay this escapade into a lucrative book deal. Otherwise, it’s hard to make sense of his actions.
March 15, 2003
QPopper Vulnerability
Yuck. Is there no rest for the weary?
According to this Bugtraq thread, there’s a buffer-overflow in qpopper 4.0.4. Qualcomm has released qpopper 4.0.5 to fix the vulnerability.
March 14, 2003
Courseware
Elizabeth Lane-Lawley takes a look at open-source courseware. Inspired by the suggestions in the comments thread, I took a little twirl through some of the offerings and came back rather disappointed. None of them have the power and flexibility that MovableType brings to weblogging software.
What makes MT great is that it is template-driven, with a clean separation between function and presentation, and between “administrative” and “user” interfaces. It doesn’t matter whether your site is baked (purely static pages) or fried (dynamic pages, generated on the fly) using php or something in between. Everything from the overall structure to the minutiae of styling is easily customized. And with a well-thought-out plugin API, there’s a lively community busily adding plugins for new functionality.
One of the more promising-looking courseware packages is Moodle. Right now, it’s user-friendly, but quite inflexible (so much is hard-coded into the modules). The author has bold plans for Moodle 2.0 (XML, XSL and CSS), which should be very exciting. If they come to fruition, it could be pretty neat.
In the meantime, I will persist in my palaeolithic ways, painstakingly chiselling hieroglyphs into stone (or something like that). Hey! After the recent scandal, at least I have SSL enabled on golem now.
March 12, 2003
God’s Favourite Breakfast Cereal
The New York Times is reporting on a recent preprint on astro-ph. The title is the rather humdrum, “A high resolution foreground cleaned CMB map from WMAP”. You might wonder why this makes it to the Times Science pages. I’ll cut to the chase, so you don’t have to slog through the usual painful Times reportage. The fuss is about the last paragraph in the paper,
What does this all mean? Although we have presented these low multipole results merely in an exploratory spirit, and more thorough modeling of the foreground contribution to l = 2 and l = 3 is certainly warranted, it is difficult not to be intrigued by the similarities of Figure 13 with what is expected in some non-standard models, for instance ones involving a flat “small Universe” with a compact topology as in [64–69] and one of the three dimensions being relatively small (of order the Horizon size or smaller). This could have the effect of suppressing the large-scale power in this particular spatial direction in the same sense as is seen in Figure 13. As so often in science when measurements are improved, WMAP has answered old questions and raised new ones.
Closing the Barn Door …
As reported earlier, 55,200 (give or take) names, addresses, and Social Security numbers were stolen from an unprotected database on the UT Administrative system. The “hack,” apparently, was nothing more sophisticated than submitting a query for a Social Security Number and seeing if the database returned a record.
Search warrants were issued, and there were police raids this weekend. But no arrests have followed.
In need of doing something, ITS has been searching through Google for UT web sites with Social Security numbers on them and peremptorily shutting them down. A colleague of mine was in the habit of posting his student grades online. Stupidly (security-consciousness is, alas, not his forté), he left the data file readable, which means that ITS shut his computer off from the 'net for three days.
I’ll come clean here.
I, too, have allowed students to retrieve their grades by entering their student ID number (aka their SSN) in a web form. The database is not retrievable, but the web form could be brute-forced exactly like that UT database. All I can say in my defence is that the effort required to brute-force it would be the same, but the maximum potential yield would be 40-50 SSN’s rather than several million. And the data for any given course is only available for a couple of months. Together, I think it’s fair to say that these make the attack unfeasible. But …
I’d love to key my database to something else. I’m still waiting for the day when student class rosters are keyed to ID numbers other than the students’ Social Security Numbers.
“Hello? ITS … when you can spare the time …”
March 11, 2003
Some Physics Notes
David Berenstein has a followup to his previous paper discussing the application of Dijkgraaf-Vafa techniques to supersymmetric gauge theories with moduli spaces of vacua.
Most of the applications to date have been to theories with isolated vacua. Understanding the vacuum structure of such theories is interesting but it is in some sense more challenging to study theories with continuous moduli spaces of vacua. In particular, it’s interesting to understand the quantum modifications to the geometry (indeed, to the topology) of the “classical” moduli space.
David studies deformations of SYM by a superpotential of the form
where
( and is SYM.)
In the corresponding matrix model, the loop equations degenerate, and David actually turns matters around to use information about the quantum-corrected moduli space of the gauge theory to provide a conjectured solution to the matrix model.
Strominger and Thompson write about “quantum violations” of the Bousso entropy bound. At first blush, this is a rather surprising subject, as the statement, by Hawking and Bekenstein, that a black hole has a temperature and an entropy, is an intrinsically quantum-mechanical one. One would have thought that Bousso’s bound, like Bekenstein’s , already incorporated the effects of quantum mechanics.
Well, in the black hole case, there is the assumption that the black hole has a well-defined mass (and hence a well-defined temperature), which is true only in the semiclassical regime, i.e. for large-enough black holes. Moreover, even semiclassically, one must count the entropy carried by the outgoing Hawking radiation in the “generalized second law of thermodynamics”
where is the area of the event horizon, is the entropy of the outgoing Hawking radiation and is the entropy carried by the matter falling into the black hole.
The “classical” Bousso bound (as proven by Flanagan, Marolf and Wald) is the generalization of the above inequality without the second term on the left hand side. Strominger and Thompson make a proposal for this missing term.
Finally, Basu and Sethi have a paper on (0,2) gauged linear -models (a subject dear to my heart). They argue that worldsheet instantons do not generate a (worldsheet) superpotential in such theories. I’ve only ever looked the conformally-invariant case (i.e., where the GLM flows to a (0,2) SCFT in the infrared) where — in all the examples I’ve ever looked at — this is perfectly obvious. They’re more interested in “massive” models where, perhaps, there’s something to prove. Though, I have to say, since the theory is strongly-coupled in the IR, I don’t see the relevance of the dilute instanton gas approximation. Moreover, at least in the (2,2) case, I’m fairly sure there is the analogue of a Veneziano-Yankielowicz superpotential generated. In the (0,2) case, there isn’t enough supersymmetry to protect the result, but I doubt that you get “zero”.
Anyway, they then go on to try to adduce, from the absence of an induced worldsheet superpotential, evidence for the nonperturbative nonrenormalization of the Fayet-Iliopoulos parameter, (i.e., in the string theory context, for the absence of a spacetime superpotential). Sigh! I tried to warn them …
March 7, 2003
Die, Blimp, Die!
March 6, 2003
Speaking of Back Ends
“No, I don’t want my payroll data available online.”
“No, I don’t want the PIN for my online Annual Benefits Enrollment emailed to me in cleartext (with a new PIN emailed to me every time I go to the web site to change the old ‘exposed’ one).”
(Perhaps the ’bot I wrote to automatically change my PIN the instant the email containing the old one arrives was what convinced them to modify their software to allow people to “opt out” of having their PIN sent via email. Probably, I flatter myself.)“No I don’t want a ‘high assurance’ UTEID to use on your javascript-based UTDirect site (where we’re just one Cross-Site Scripting vulnerability away from disaster)”
I should not have worried. Why bother hacking the front-end when the University leaves a back-end database wide open to anyone on the internet? (For some reason, ITS has an aversion to firewalls.)
So, over the weekend, someone stole 55,000 names, addresses, and Social Security numbers. They hit the database server so hard that it crashed under the load (which is how the crack was discovered).
Now the University’s set up a web site for the victims and are working closely with law-enforcement to recover the stolen data. According to the Austin American Statesman, they’ve traced the attacks to computers in Austin and Houston. But, it seems to me that unless the hackers were incredibly stupid, those machines were just launchpads, and their innocent owners are about to get a rude awakening when the cops come busting through their front doors in the middle of the night.
But what do I know?
The Back End
In the interests of greater efficiency and data integrity, I converted to a MySQL backend from the default Berkeley DB.
If you want to try that, and have implemented ThreadedComments, be sure to modify the database schema before running mt-db2sql.cgi (i.e., don’t make the same mistake I did).
You need to add two columns and an index to the database:
--- schemas/mysql.dump.orig Thu Mar 6 12:45:41 2003 +++ schemas/mysql.dump Thu Mar 6 12:48:05 2003 @@ -80,12 +80,15 @@ comment_email varchar(75), comment_url varchar(255), comment_text text, + comment_subject text, + comment_parent_id integer, comment_created_on datetime not null, comment_modified_on timestamp not null, comment_created_by integer, comment_modified_by integer, index (comment_created_on), index (comment_entry_id), + index (comment_parent_id), index (comment_blog_id) );
Anybody know how stable MySQL 3.23.55 is under MacOSX? Will I need to check periodically to see if the daemon has died?
Update: A couple of things did break.
<$MTEntryBody smarty_pants="2" process_tags="1"$>worked before the upgrade, but caused rebuilds to fail after upgrading. Re-ordering it to<$MTEntryBody process_tags="1" smarty_pants="2"$>fixed the problem (you can imagine how long it took to figure this one out!).- The mt-rssfeed plugin now requires an explicit choice of directory where the RSS feeds are cached. It defaulted to the
dbdirectory when using Berkeley DB. But now, with no path specified, rebuilds would “work,” but no RSS feeds would appear.
March 4, 2003
Bigger, Faster, Harder
(That should garner some “interesting” google queries.)
So my iBook started acting up again. I thought I had cured it, but recently, the symptoms began to recur. And they got worse. When rebooting the machine, it sometimes would take a half dozen attempts before the hard drive would spin up. Uh oh! Seems that the hard drive was slowly heading south.
So, to replace the original 15GB, 4200RPM IBM Travelstar 40GN, I bought a new 40GB, 5400RPM Travelstar 40GNX. I threw in another $50 for an external Firewire case, and cloned my old drive onto the new one with CarbonCopyCloner before bringing them into the shop for the old switcheroo.
I would have done it myself ('cuz I’m that kinda guy), but these instructions, posted to the net by some kind soul dissuaded me. Replacing the hard drive requires removing 30 (!) screws and completely disassembling the machine. (“If you’ve removed more than 30 screws… good for you! But I can’t help you put them all back” say the instructions.)
I had a bit of a fright when, after the installation, the iBook wouldn’t boot at first (“Looks like you need a new logic board,” said the tech) but then I remembered that I had to boot into open firmware (option +O +F while powering up) to reset the startup volume. Now all is good — except that the aforementioned tech seems to have lost one of the little rubber feet.
Grrr…
March 3, 2003
Gremlins
Sorry if access to this blog has been flaky recently (slow page loads/images not loading properly).
Should be fixed now…
March 1, 2003
A Pound of Flesh
Good old D2 does a bang-up job with an economic analysis of Ezra Pound’s Canto 45.
It’s a very entertaining blog, whose current recurring theme is “Shorter den Beste”, a wickedly pithy sendup of USS Clueless.

 Posts with this logo use
Posts with this logo use