Math and Mass Surveillance: A Roundup
Posted by Tom Leinster
The Notices of the AMS has just published the second in its series “Mathematicians discuss the Snowden revelations”. (The first was here.) The introduction to the second article cites this blog for “a discussion of these issues”, but I realized that the relevant posts might be hard for visitors to find, scattered as they are over the last eight months.
So here, especially for Notices readers, is a roundup of all the posts and discussions we’ve had on the subject. In reverse chronological order (and updated after the original appearance of this post):
- The Heilbronn Institute and the University of Bristol
- NSA axes math grants
- Five quickies
- Turing’s legacy
- New evidence of the NSA deliberately weakening encryption
- More on the AMS and NSA
- The AMS must justify its support of the NSA
- Turing’s legacy
- New evidence of the NSA deliberately weakening encryption
- Why it matters
- Should mathematicians cooperate with GCHQ? Part 3
- Should mathematicians cooperate with GCHQ? Part 2
- New Scientist article
- Big data power
- Should mathematicians cooperate with GCHQ?
- The deteriorating relationship between mathematicans and the NSA
- The Electronic Frontier Foundation at the joint meetings
- Academics against mass surveillance
- Severing ties with the NSA.

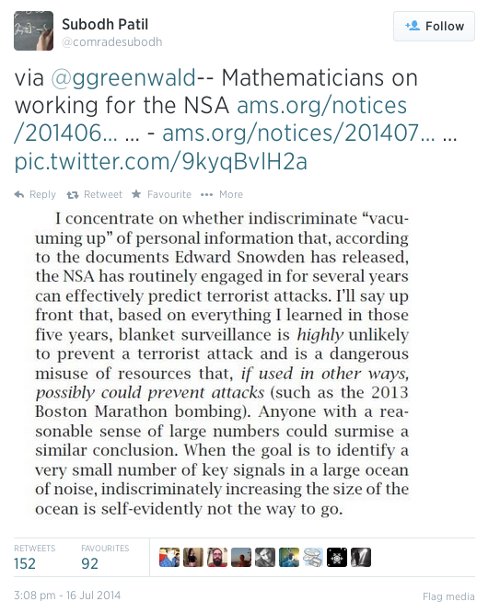
Re: Math and Mass Surveillance: A Roundup
The AMS ought to be ashamed of itself for publishing such a deceptive, specious, and self-serving column. Richard George makes vague references to unsupported allegations that the NSA weakened crypto standards–and such purposeful vagueness is his only hope of persuasion, given that the evidence we have at hand overwhelmingly supports the conclusion that the NSA engaged in misconduct.
In particular, the New York Times claimed in 2013 that some of the documents released by Edward Snowden “suggest that the N.S.A. generated one of the random number generators used in a 2006 N.I.S.T. standard — called the Dual EC DRBG standard — which contains a back door for the N.S.A,” a conclusion which has been largely acknowledged as overwhelmingly plausible, given the evidence at hand.
Moreover, the NSA’s 2013 budget request, also published in part by the New York Times, describes an NSA program with a stated aim to “insert vulnerabilities into commercial encryption systems, IT systems, networks, and endpoint communications devices used by targets.” I am no cryptographic expert, but this seems unambiguously to declare that the NSA is in fact in the business of weakening cryptographic systems and protocols.
After his various falsehoods, George ends his column with ad hominem attacks against those who have released this information to the public, beginning with his strange declaration that he and his colleagues are “disappointed” and have “a feeling of betrayal” from Snowden & al. (Why should we care how he and his fellow NSA employees feel when the issue at hand is whether they are participating in injustice?), and ending with the oft-repeated claim that such defectors have done “immense” damage–a claim that Snowden’s allies are fond of making yet in support of which they find themselves unable to cite even a single example.
Finally, in the course of his denunciation of the leakers, George misgenders Chelsea Manning–referring to her as Bradley, a name she has since renounced–, a woman who has made the incredibly brave decision to publicly announce her gender identity while incarcerated in a men’s military prison which offers no support for gender dysphoria. Even those who, like George, believe Manning’s contribution to her country to be traitorous rather than heroic ought to have the basic decency to respect her gender identity and the difficulties she has suffered and continues to suffer as a trans woman.